Access management
API keys
Each Pinecone project has one or more API keys. In order to make calls to the Pinecone API, a user must provide a valid API key for the relevant Pinecone project. You can manage API key permissions in the Pinecone console. The available permission roles are as follows:General permissions
- Pinecone console
- API
| Role | Permissions |
|---|---|
| All | Permissions to read and write all project data. |
Control plane permissions
- Pinecone console
- API
| Role | Permissions |
|---|---|
| ReadWrite | Permissions to list, describe, create, delete, and configure indexes, backups, collections, and assistants. |
| ReadOnly | Permissions to list and describe indexes, backups, collections, and assistants. |
| None | No control plane permissions. |
Data plane permissions
- Pinecone console
- API
| Role | Permissions |
|---|---|
| ReadWrite |
|
| ReadOnly |
|
| None | No data plane permissions. |
Organization single sign-on (SSO)
SSO allows organizations to manage their teams’ access to Pinecone through their identity management solution. Once your integration is configured, you can require that users from your domain sign in through SSO, and you can specify a default role for teammates when they sign up. SSO is available on Standard and Enterprise plans. For more information, see configure single sign on.Role-based access controls (RBAC)
Pinecone uses role-based access controls (RBAC) to manage access to resources. Service accounts, API keys, and users are all principals. A principal’s access is determined by the roles assigned to it. Roles are assigned to a principal for a resource, either a project or an organization. The roles available to be assigned depend on the type of principal and resource.Service account roles
A service account can be assigned roles for the organization it belongs to, and any projects within that organization. For more information, see Organization roles and Project roles.API key roles
An API key can only be assigned permissions for the projects it belongs to. For more information, see API keys.User roles
A user can be assigned roles for each organization they belong to, and any projects within that organization. For more information, see Organization roles and Project roles.Compliance
To learn more about data privacy and compliance at Pinecone, visit the Pinecone Trust and Security Center.
Audit logs
To enable and manage audit logs, you must be an organization owner. This feature is available only on Enterprise plans.
JSON
- Organization events
- Project events
- Index events
- User and API key events
- Security and governance events
Organization events
| Action | Query parameters |
|---|---|
| Rename org | event.action: update, event.resource_type: organization, event.resource_id: NEW_ORG_NAME |
| Delete org | event.action: delete, event.resource_type: organization, event.resource_id: DELETED_ORG_NAME |
| Create org member | event.action: create, event.resource_type: user, event.resource_id: [ARRAY_OF_USER_EMAILS] |
| Update org member | event.action: update, event.resource_type: user, event.resource_id: { user: USER_EMAIL, role: NEW_ROLE } |
| Delete org member | event.action: delete, event.resource_type: user, event.resource_id: USER_EMAIL |
Project events
| Action | Query parameters |
|---|---|
| Create project | event.action: create, event.resource_type: project, event.resouce_id: PROJ_NAME |
| Update project | event.action: update, event.resource_type: project, event.resource_id: PROJECT_NAME |
| Delete project | event.action: delete, event.resource_type: project, event.resource_id: PROJECT_NAME |
| Invite project member | event.action: create, event.resource_type: user, event.resource_id: [ARRAY_OF_USER_EMAILS] |
| Update project member role | event.action: update, event.resource_type: user, event.resource_id: { user: USER_EMAIL, role: NEW_ROLE } |
| Delete project member | event.action: delete, event.resource_type: user, event.resource_id: { user: USER_EMAIL, project: PROJ_NAME } |
Index events
| Action | Query parameters |
|---|---|
| Create index | event.action: create, event.resource_type: index, event.resouce_id: INDEX_NAME |
| Update index | event.action: update, event.resource_type: index, event.resource_id: INDEX_NAME |
| Delete index | event.action: delete, event.resource_type: index, event.resource_id: INDEX_NAME |
| Create backup | event.action: create, event.resource_type: backup, event.resource_id: BACKUP_NAME |
| Delete backup | event.action: delete, event.resource_type: backup, event.resource_id: BACKUP_NAME |
User and API key events
| Action | Query parameters |
|---|---|
| User login | event.action: login, event.resource_type: user, event.resouce_id: USERNAME |
| Create API key | event.action: create, event.resource_type: api-key, event.resource_id: API_KEY_ID |
| Delete API key | event.action: delete, event.resource_type: api-key, event.resource_id: API_KEY_ID |
Security and governance events
| Action | Query parameters |
|---|---|
| Create Private Endpoint | event.action: create, event.resource_type: private-endpoints, event.resource_id: PRIVATE_ENDPOINT_ID |
| Delete Private Endpoint | event.action: delete, event.resource_type: private-endpoints, event.resource_id: PRIVATE_ENDPOINT_ID |
Data protection
Customer-managed encryption keys (CMEK)
This feature is in public preview.
Backup and recovery
This feature is in public preview and available only on Standard and Enterprise plans.
Encryption at rest
Pinecone encrypts stored data using the 256-bit Advanced Encryption Standard (AES-256) encryption algorithm.Encryption in transit
Pinecone uses standard protocols to encrypt user data in transit. Clients open HTTPS or gRPC connections to the Pinecone API; the Pinecone API gateway uses gRPC connections to user deployments in the cloud. These HTTPS and gRPC connections use the TLS 1.2 protocol with 256-bit Advanced Encryption Standard (AES-256) encryption.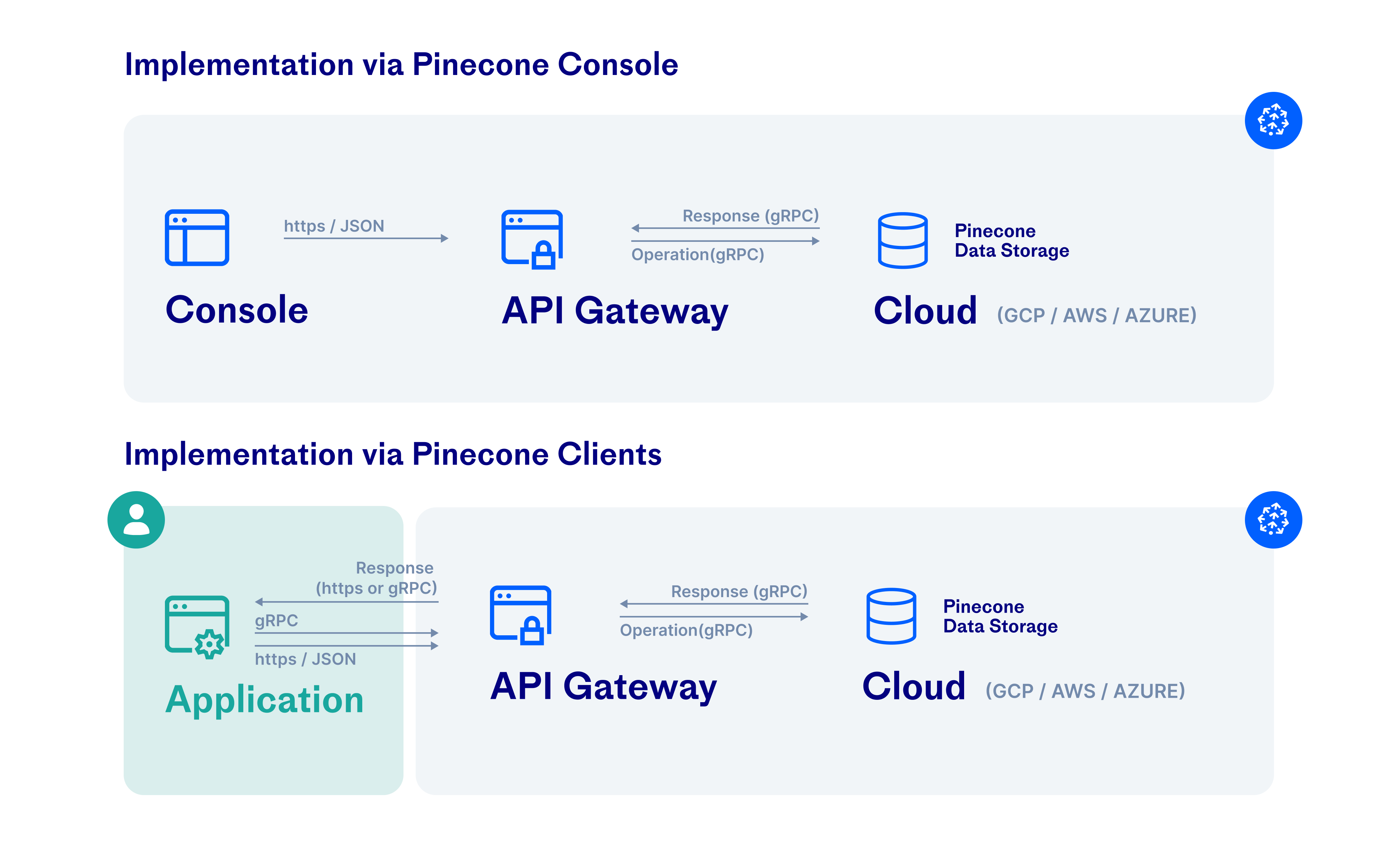
Network security
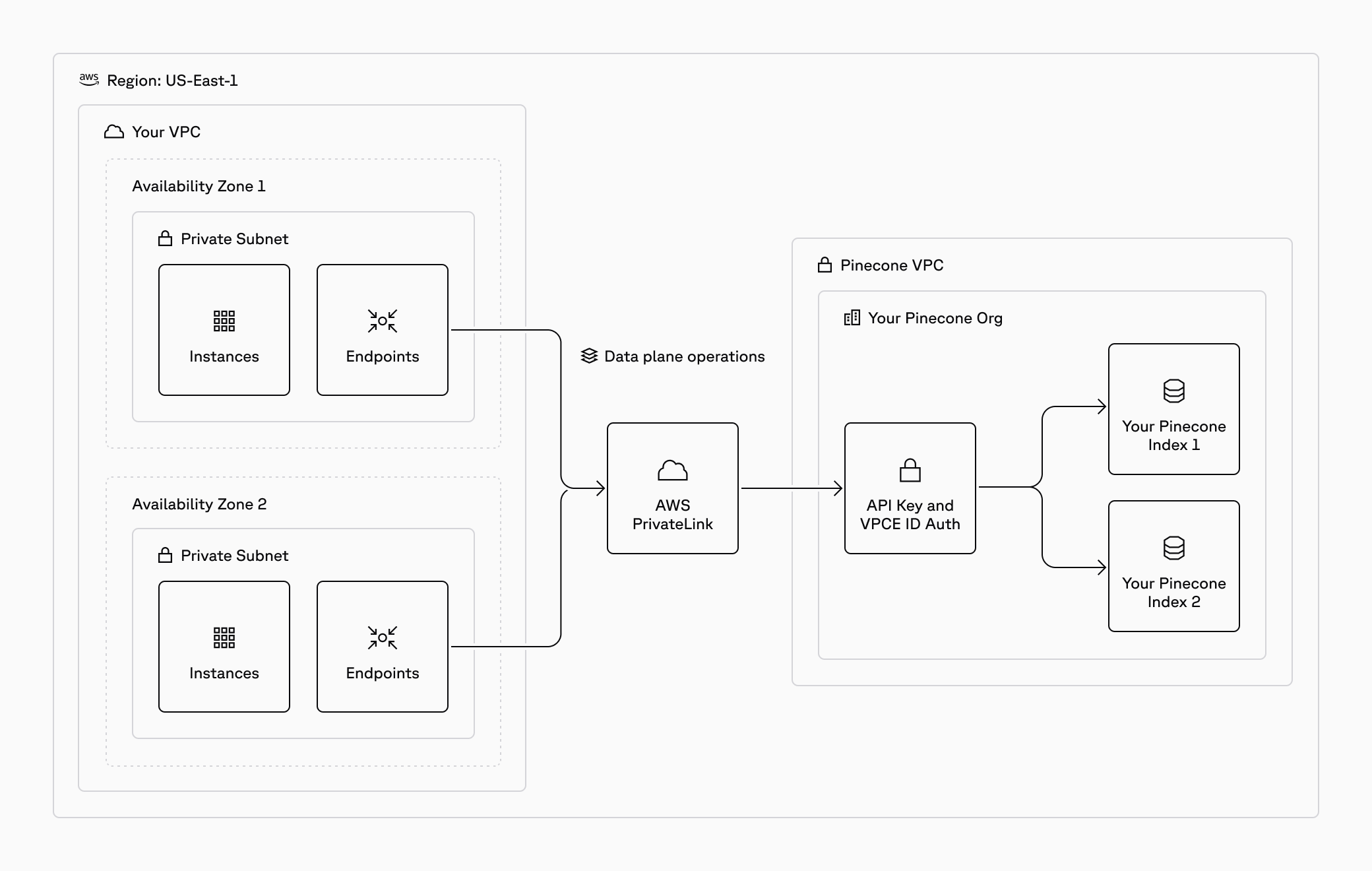
Private Endpoints for AWS PrivateLink
Use Private Endpoints to connect to Amazon Web Services (AWS) PrivateLink. This establishes private connectivity between your Pinecone serverless indexes and supported AWS services while keeping your VPC private from the public internet.